views
Protecting Your Passwords
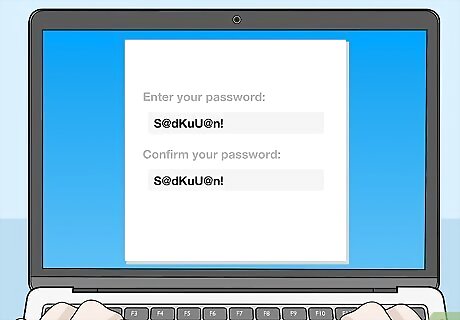
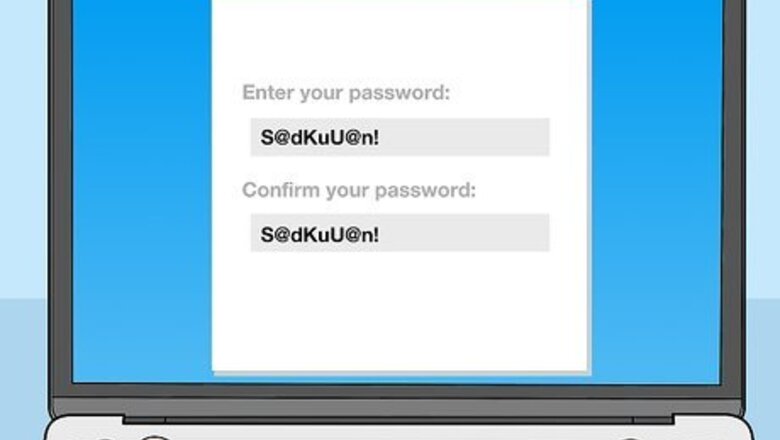
Use strong, unique passwords. When you’re creating a password for your account, make sure to include a mix of numbers, symbols, and letters, both uppercase and lowercase. Avoid using the same passwords for multiple accounts. It’s harder to remember, but it will keep your information much safer. Try abbreviating a phrase. For example, “Soda at dinner keeps you up at night” could become “S@dKuU@n!” Longer passwords are always stronger, so try using a favorite quote, or a line from a song, book, or movie. Remember that some websites have password length restrictions, so make sure to follow those as well. Avoid using common passwords like “123456” or “password,” or information about you that others might easily be able to find out, like a nickname, your favorite sport, or your pet's name. Also, don’t use the same password on multiple sites as this can increase the likelihood of being hacked.
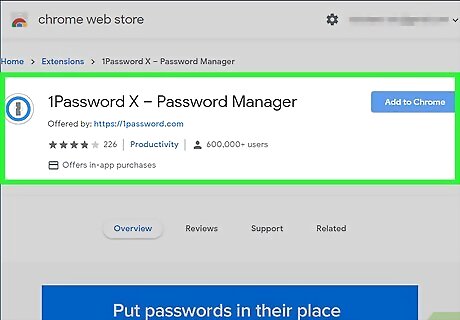
Use a password manager to keep passwords safe and organized. Password managers automatically generate and store strong, unique passwords for each of your accounts. You’ll simply create one master password for the manager and let it keep all the others safe. You can use some password managers for free, while more premium options are available for a fee. Popular, trustworthy password managers include 1Password and LastPass. You can find others by searching for them online. You can also use your browser’s built-in password syncing service, although it’s considered less safe and more vulnerable to hacking, so use with caution.
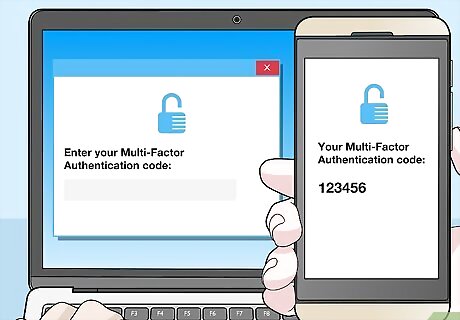
Enable multi-factor authentication on your accounts. Multi-factor authentication makes an account even more secure by requiring extra information to let you log in, such as a code sent to your phone. Many large email providers and social media accounts offer this service. To check whether an account has multi-factor authentication, check the site’s Settings page. This extra step might seem annoying, but it will keep your information safer than just a password alone. EXPERT TIP Brandon Phipps Brandon Phipps Technology Specialist Brandon Phipps is a Technology Specialist based in Bakersfield, CA. He is the owner of Second Star Technologies and specializes in Managed IT Services for small and mid-sized businesses in Bakersfield, CA. With over 23 years of experience, he offers expert cloud computing, cybersecurity, and network management solutions. Brandon is a committed community member and coach who leads and innovates in tech and sports coaching. His dedication to local businesses and communities is evident in his hands-on, tailored approach to IT solutions. Brandon Phipps Brandon Phipps Technology Specialist Enable two-factor authentication on all your digital accounts. That applies to all your personal accounts, business accounts, finances, client information, and productivity apps. Two-factor authentication protects your sensitive data from unauthorized parties and reduces the risk of security breaches.
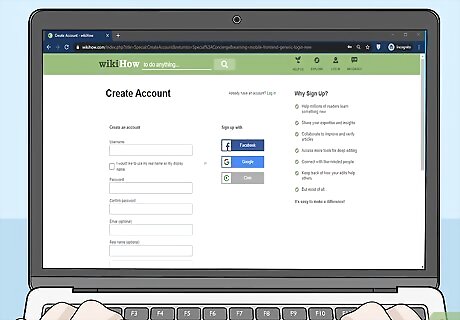
Sign up for accounts on legitimate sites only. Consider very carefully before you make an account on a website, even if it just requires giving your email address. No matter how secure your passwords are, using them on unsafe sites will put your information in danger. Avoid sites with misspellings or bad grammar in their addresses, which could be dangerous copycats of legitimate websites. Also look out for sites that have lots of pop-ups, or numbers or gibberish in their addresses.
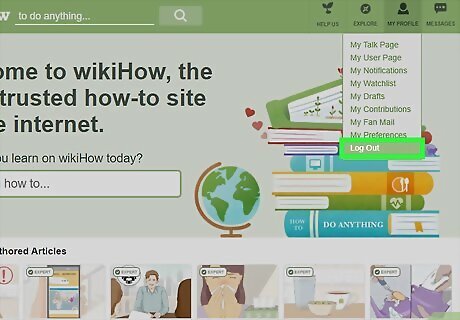
Log out of sites when you’re done using them. Logging into a site creates a cookie in your browser, which identifies you and, if stolen, can compromise your account. This is especially an issue on sites that hold sensitive information, like your bank account or credit card number, so it’s always best to log out once you’re finished. Log out of any site you use on a public computer or network. Log out of any online banking or shopping site you use, even on your home computer and network. It’s typically OK to keep your home computer logged on to accounts like your email or social media, as long as you make sure to lock your computer if you ever step away from it.
Using Social Media and Email Safely
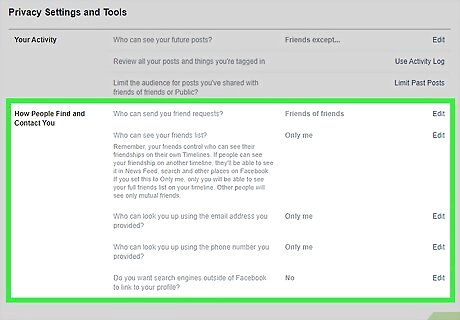
Make your profiles private. Keeping your social media profiles private can make it harder for strangers to contact you online or get ahold of your information. Choose an option that makes your profile visible to only you or your friends. And even then, do not trust privacy settings to make your account private. Go to your account settings and your security or privacy menu to view and change your privacy level. Even if you choose to keep your profile public, make sure that crucial information, like your address and phone number, is hidden.
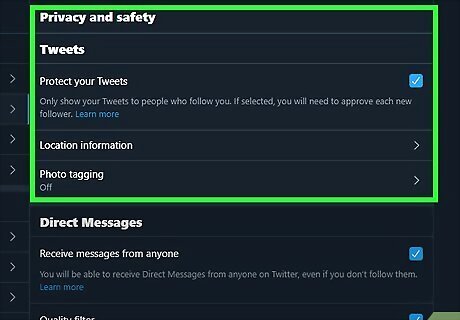
Review what information is public on your social media profiles. Important information on your account can slip through the cracks and be made public, especially if you recently made or edited your profile. Head to the Privacy section of your account to check what’s currently accessible by people who aren’t your friends. Do this every few months or so to make sure that everything you want to be private stays that way.

Think about whether you’ll regret posting something later. Part of being safe on the Internet is knowing what is and isn’t OK to post. It might feel fine in the moment to post something inappropriate or provocative, but remember that those posts can be screenshotted, seen, and shared by people all over the world, even if you delete them. As a rule of thumb, ask yourself if your post is something you’d want your (grand)parents, teachers, or future employers to see. If the answer is no, don’t post. This is known as the "grandma rule".
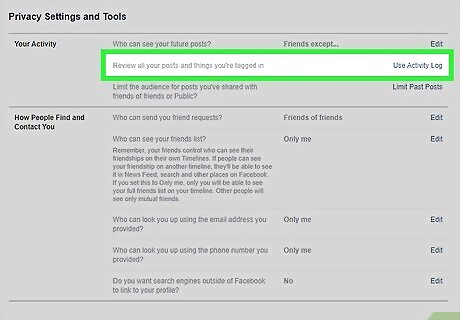
Review posts you’re tagged in before approving them. You can prevent something harmful or embarrassing from being linked to your account by turning on tag review. This is especially important if your friends’ accounts aren’t set to private; a post or image they tag you in could be seen by anyone. Turn on tag review in your privacy settings. You’ll get a notification when someone tags you in a post, then have the option to approve the tag and put the post on your own account, or to deny it. If you’re still concerned about a photo even after removing your tag, talk to the poster about taking it down.

Never give personal information to someone you met online. This might seem obvious, but it’s still important to remember. No matter how well you may think you know someone you met online, you can never really be sure of who they are and whether they might be dangerous. Avoid giving out contact information like your name, address, or phone number, as well as other information that might make it easy to find you, like your school or workplace. EXPERT TIP Scott Nelson, JD Scott Nelson, JD Police Sergeant, Mountain View Police Department Scott Nelson is a Police Sergeant with the Mountain View Police Department in California. He is also a practicing attorney for Goyette & Associates, Inc. where he represents public employees with a myriad of labor issues throughout the state. He has over 15 years of experience in law enforcement and specializes in digital forensics. Scott has received extensive training through the National Computer Forensics Institute and holds forensic certifications from Cellbrite, Blackbag, Axiom Forensics, and others. He earned a Master of Business Administration from the California State University Stanislaus and a Juris Doctorate from the Laurence Drivon School of Law. Scott Nelson, JD Scott Nelson, JD Police Sergeant, Mountain View Police Department Our Expert Agrees: In addition to obvious information that can tell someone where you live (like your school or workplace), make sure not to tell strangers things like your favorite local restaurant, park, or store. This information can be used to get a general idea of where you live.

Use caution when meeting in-person with someone you met online. It’s best not to meet people in-person who you’ve only talked to online, but some situations might require it—if you sold something on Craigslist, for example, or are using an online dating site. In these cases, meet in a public place and bring a friend with you. If you can’t bring a friend, tell someone where you’ll be, who you’ll be with, and for how long. If you’re under 18, never agree to meet someone in-person who you met online.
Use gender-neutral pseudonyms on forums. Even private or invite-only forums can be more dangerous than traditional forms of social media, so take extra care to protect your identity. Use a gender-neutral pseudonym if you can, and avoid posting pictures of yourself or linking to your other social media.
Don’t open emails or files from people you don’t know. Phishing scammers are people who use fake emails or messages to make you share personal information. If you see an email from an unfamiliar address, or from an address you know but with a suspicious message, move it to your spam folder. The email could also include links that might look legitimate, but never click on them until you can verify that it’s a legitimate message. If you know the person whose email was being used, tell them that their account has been hacked and report the phishing by filing a complaint with the FBI’s Internet Fraud Complaint Center at www.ic3.gov. Phishing scammers are often after your bank account or Social Security number, so be extra cautious if you get an email requesting money, login credentials, or very personal information.
Using Safe Sites and Networks
Avoid clicking on sites that look fake or scammy. If you’re even somewhat familiar with the Internet, chances are you can recognize bad links when you see them: bad grammar, popups, “click bait” headlines, or a false-looking web address. Avoid clicking on these sites and never download anything from them. Spending time on these kinds of websites can give your computer a virus or make it crash.
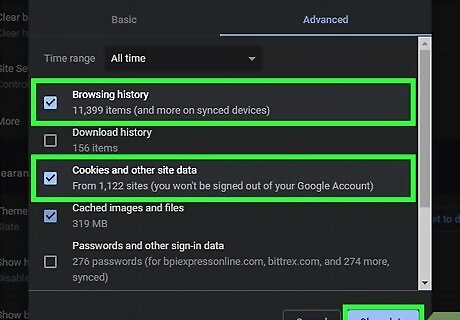
Clear your browsing history often to maintain your privacy. Many sites have access to your cookies, small text files that record your preferences and let sites respond to them, often to show you more relevant ads. However, cookies can also be used by hackers as a way to get your personal information. Clear your cookies every month or so to wipe out any personal information in them.

Do online shopping on encrypted sites. When you’re shopping online or logging into your online bank account, check the URL to make sure it starts with “https” instead of “http.” The “s” means that the website is secure and encrypts your data so it can’t be stolen. Secure sites should also have a small lock icon in the URL field. Although it’s convenient to save your payment information on a shopping site, always do so with caution, as this puts you at risk if the site gets hacked.

Use private WiFi networks, never public ones. Public WiFi—like the kind you might find at restaurants, hotels, or airports—is often unsecured, making it easier for someone to hack into your computer. Only connect to an unsecured network if you absolutely have to, and be aware of the risks it could come with. If you often need WiFi on the go, try buying a virtual private network (VPN), a piece of hardware that can create a secure, private connection from anywhere. Connect with care on your smartphone, too. If you can, confirm the name and login requirements of the WiFi with appropriate staff before connecting.
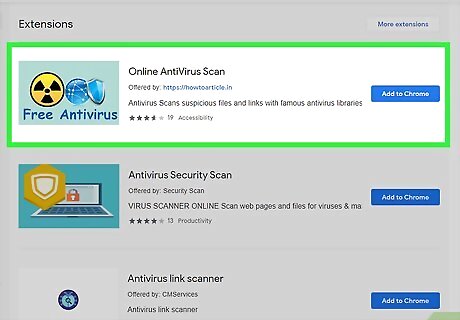
Use an antivirus extension on your browser. For extra safety on the Internet, you can download an antivirus extension to check the security of a site or block pop-up ads with viruses or malicious content. Remember to download only from a legitimate source, like the Chrome webstore, to ensure that the extension is safe.
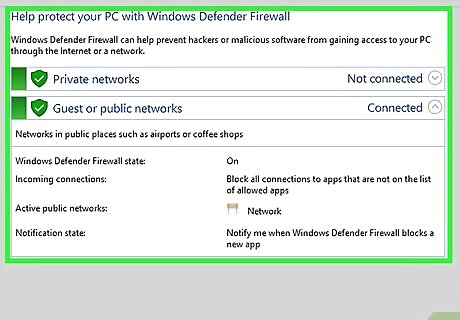
Install a firewall to protect your home network. A firewall is an electronic barrier that prevents unauthorized devices from getting access to your computer or phone. Many computers come pre-loaded with a firewall; go to your computer’s security section to check if yours has one. For a fee, you can also download firewall software from authorized sellers like Norton, McAfee, or Microsoft.
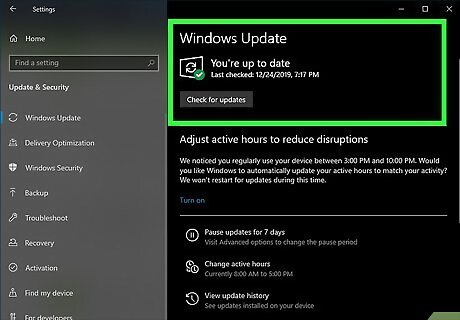
Keep your computer’s software up to date. Most software updates come with security upgrades, so it’s important that you have the latest version at all times. To easily download updates as soon as they come out, turn on automatic updates in your computer’s Settings.
Staying Safe on Your Smartphone
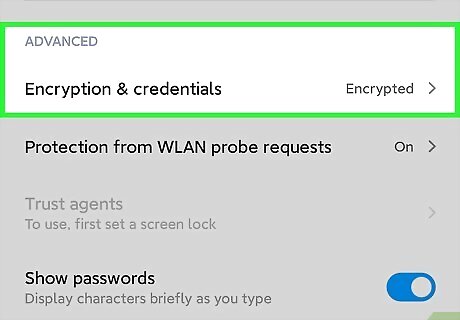
Enable encryption software on your phone. Many smartphones come encrypted, meaning that their software scrambles your information so it can’t be accessed by unauthorized users. To check if your phone is encrypted, go to its settings and click on the security tab. Automatically encrypted phones include iPhones, newer Androids, and Google’s Pixel phones. You can enable encryption software on your Android in its security menu. For extra protection, you can download encryption applications from the app store. EXPERT TIP Brandon Phipps Brandon Phipps Technology Specialist Brandon Phipps is a Technology Specialist based in Bakersfield, CA. He is the owner of Second Star Technologies and specializes in Managed IT Services for small and mid-sized businesses in Bakersfield, CA. With over 23 years of experience, he offers expert cloud computing, cybersecurity, and network management solutions. Brandon is a committed community member and coach who leads and innovates in tech and sports coaching. His dedication to local businesses and communities is evident in his hands-on, tailored approach to IT solutions. Brandon Phipps Brandon Phipps Technology Specialist Encryption is essential to maintain security and avoid disastrous consequences. Encrypt sensitive systems with client and financial data to restrict access to authorized users only. Act promptly and keep this practice in the future.
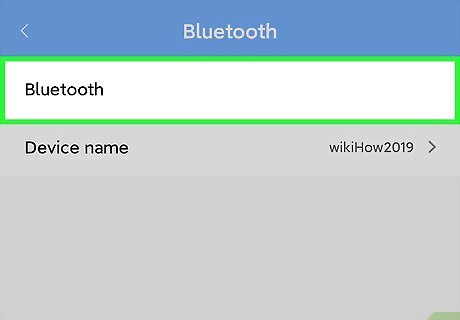
Set your Bluetooth to “non-discoverable.” Although your phone’s Bluetooth isn’t as easy to hack into as a wireless network, hackers can still use it to access your phone remotely when they’re in range. To prevent this, set your Bluetooth’s default to “non-discoverable” so you don’t pop up on hackers’ radar. If you see an unknown Bluetooth request to pair with your device, ignore or deny it right away. Take extra care in crowded areas where potential hackers are within range of your Bluetooth, such as restaurants and public transportation.

Download apps from verified stores only. The easiest way for viruses to get into your phone is through downloads like apps. “Official” stores like the Apple app store or the Google Play store can typically be considered safe places to buy apps, but you should never download one from any other site. Remember to read over the requirements, terms, and conditions an app has before you install it. This will be long and probably boring, but it’s important that you know exactly what is being installed onto your device.
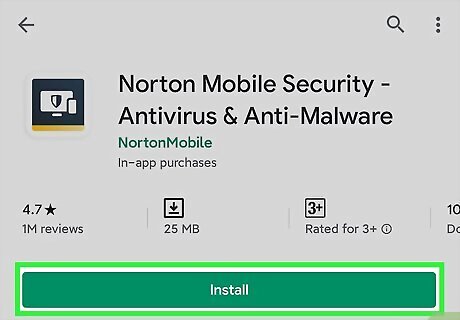
Download security software for extra protection. For the most reliable smartphone protection, you can buy a mobile security package. These tools typically come with a firewall and spam protection, as well as GPS tracking to help you find a lost or stolen device. Some security packages also come with remote locking capabilities to prevent a stolen phone from being used.















Comments
0 comment