views
Choosing a Substitution Sequence
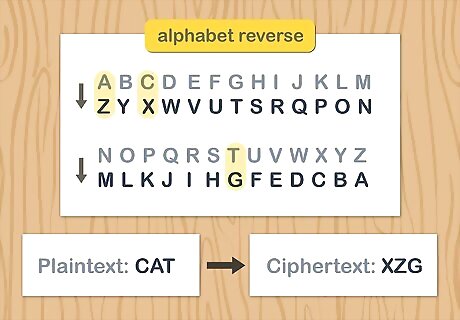
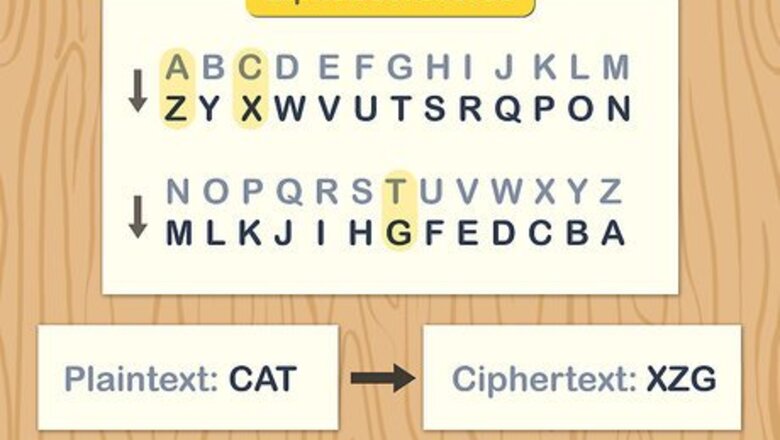
Reverse the alphabet to create a basic cipher alphabet. Substitution ciphers work by creating a disordered alphabet, allowing you to substitute letters for other letters. For a straightforward substitution cipher, simply use the alphabet backwards, so that “a” becomes “z,” “b” becomes “y,” “c” becomes “x,” and so on. This substitution cipher would read: ZYXWVUTSRQPONMLKJIHGFEDCBA. This second alphabet is often referred to as the “ciphertext.”
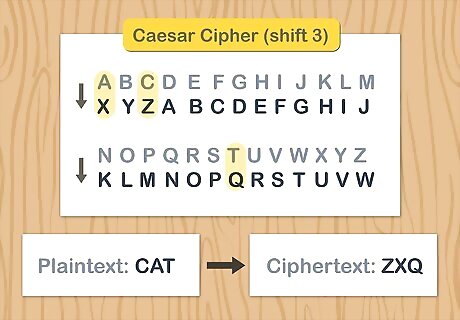
Replace every letter with the letter 3 before it for a more complex cipher. Just writing the alphabet backwards for your cipher is pretty simple and will be easy to crack. If you’d like a more complex cipher, replace every letter with the letter that comes 3 before it in the alphabet. As an easy example, using this cipher, the word “CAT” reads “ZYQ.”
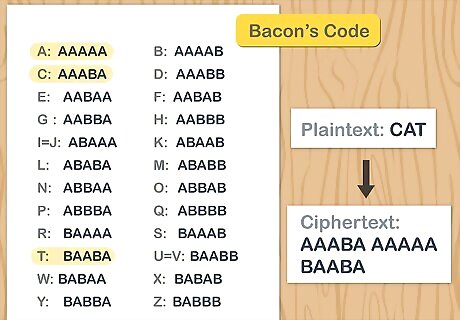
Substitute an arbitrary 5-letter sequence for each letter of the alphabet. This is known as Bacon’s Code. Bacon’s Code replaces each letter of the English alphabet with a 5-letter sequence. These sequences begin with “AAAAA” and add “B”s in an arbitrary order. So, in Bacon’s Code, A = AAAAA; B = AAAAB; C = AAABA; D = AAABB and so on. Maintain this pattern to fill in the rest of the alphabet, or make up your own 5-letter replacements. When reading messages in Bacon’s Code, pause every 5 letters to decode the letter. For example, the message “AAABAAABAAABABBABABB ABBBBAABBBABBBAABBABAABAA” reads “CELL PHONE” Encrypt messages in Bacon’s code online at: https://mothereff.in/bacon.
Notating Your Substitution Alphabet

Write the 2 alphabet sequences on a sheet of paper. Write out the standard English alphabet at the top of a sheet of paper: ABCDEFGHIJKLMNOPQRSTUVWXYZ. Then, beneath that, write out the substitution letters. Replacing every letter with the letter 3 before it instead reads: XYZABCDEFGHIJKLMNOPQRSTUVW. So, your cipher sheet would look like this: A B C D E F G H I J K L M N O P Q R S T U V W X Y Z X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
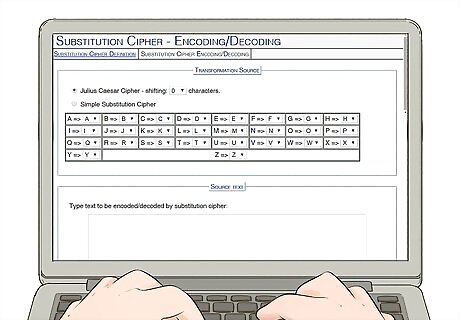
Use an online substitution generator to save paper. If you’d rather not have to laboriously write out by hand the entire cipher sequence—and each coded message—try using a cipher website. Cipher websites allow you to select which letter of the alphabet will be substituted for each other letter. Once you’ve keyed in the substitutions, you can use the cipher website to both encode and decoded messages. Find a substitution cipher generator online at: http://substitution.webmasters.sk/simple-substitution-cipher.php. Access another viable site at: http://rumkin.com/tools/cipher/substitution.php.
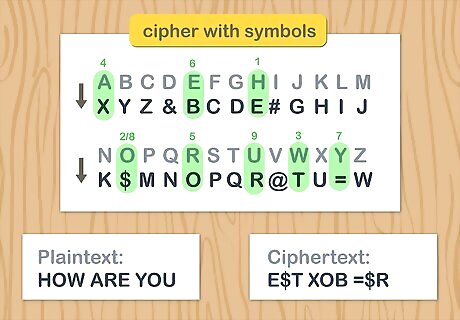
Add symbols into the cipher to make it harder to crack. If you’re worried that people (e.g., friends or parents) may try to crack your cipher, don’t limit yourself to using only letters. Introduce some symbols to your cipher. This way, encoded words will include punctuation symbols and not just letters, making them more confusing to people without the encryption code. For example, your encryption cipher with symbols could read: A B C D E F G H I J K L M N O P Q R S T U V W X Y Z. X Y Z & B C D E # G H I J K $ M N O P Q R @ T U = W. Using this cipher, the message “HOW ARE YOU” would read “E$T XOB =$R.” If this is your first time creating (or using) a substitution cipher, you might want to skip this step.
Encrypting and Decrypting Messages

Pick a word or phrase to encrypt. Before you can create an encrypted message, you’ll need text to encode. If this is your first time encoding a message using a substitution cipher, start simple. Pick a short word or 2 to encode, rather than a long paragraph. For example, try the phrase “open door.” Once you’re familiar with the encryption process, start encoding longer phrases or sentences. Online cipher encryption sites can make encoding full paragraphs much easier.
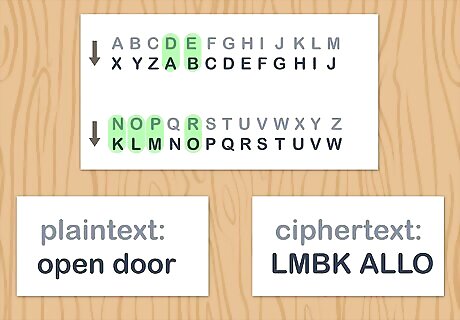
Replace each letter in the phase with a letter from the cipher alphabet. Go through your English phrase or word letter by letter and replace the English letter with the corresponding letter from your ciphertext. Find the replacement letters by identifying the English letter, then looking beneath it to find the corresponding letter in the ciphertext For example, say that you’re using the ciphertext in which you replaced each letter of the alphabet by the letter 3 before it. The English phrase “OPEN DOOR” when encoded in your ciphertext would read: “LMBK ALLO.”

Decrypt a coded message by finding the substitute for cipher letters. To translate a coded message back into English, reverse the process you used to encode a message. For each letter of the encoded message in the ciphertext alphabet, find the letter it corresponds to in the English alphabet. Write out each letter 1 at a time to decrypt the message. For example, let’s say that you’re still using the ciphertext that replaces standard alphabet letters with the letter 3 before them. If your friend passes you a code that reads “ZLLI EXQ. IRKZE PLLK?” you can use the cipher alphabet to decrypt it. You’ll discover that the message says “COOL HAT. LUNCH SOON?”
















Comments
0 comment