views
Secure Your Phone
Install security software on your Android phone. Don't download just any app. Read recommendations from trustworthy sources like Consumer Reports, CNET, and AV-TEST. Make sure that you choose an antivirus from a reputable antivirus company that you recognize, such as Norton, McAfee, Avast, or Bitdefender. Antivirus apps from reputable companies are better at detecting viruses than apps from unknown companies. For the most part, the iOS software is difficult to hack. However, some versions might have vulnerabilities. The best you can do is update your software as soon as new versions are released and be careful which apps you can install. Don't rely on Google Play Protect as your antivirus. Play Protect has performed poorly in tests. Password-protect your security software, if possible.
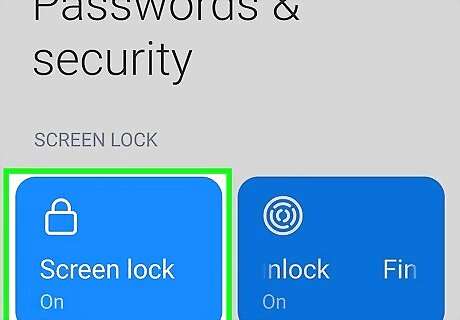
Set a passcode. Pick something that's complex, yet easy to remember. Avoid birthdays, pets' names, bank PINs, or part of your phone number. Follow the instructions at Apple or Android support to set yours up. To set a passcode for your iPhone, choose a code that consists of six digits, four digits, or an alphanumeric code you set yourself. Avoid easy unlocking methods. Don't be tricked by fingerprint- or facial recognition. Hackers can copy your fingerprints from drinking glasses or use photographs of you. Don't set your phone to automatically unlock when you're at home or when it's near other smart devices. If someone breaks into your home or gets a hold of your smart watch, your phone will be vulnerable. For an Android phone, start at the menu button from the home screen. Tap “Settings,” then “Security,” and then “Screen Lock.” The actual words might be different depending on your phone's brand name. Choose between Pattern Unlock, a personal PIN, or an alphanumeric password. After that, choose how long you want your phone to wait before locking.

Vet apps before installing them. Download apps only from a reputable seller or site, such as Apple's App Store or Google Play. Be careful if you use an Android phone. Google doesn't vet its apps as carefully as Apple. Read reviews from Consumer Reports, Wired, or CNET before downloading any third-party apps.

Make sure you know how to control your phone remotely. Settings or apps allow you to remotely lock and erase your phone if it's stolen. If you have a newer phone, you don't need to download anything. Control your iPhone through “Find My Phone” in iCloud.Remotely secure your Android phone through your Google account with Android Device Manager. If you have an older iPhone, get the Find My iPhone app from iTunes. Download Find My Phone for older Android models. Both apps are free.
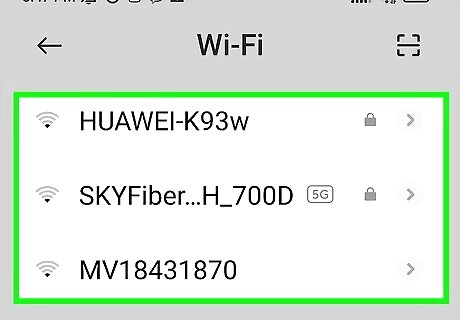
Use caution with unsecured Wi-Fi connections. Unsecured connections don't have lock icons near their listings. Avoid them, if you can, and use your phone's secure mobile connection. Otherwise, install a virtual private network (VPN), which directs your traffic through encrypted connections. Even if you're using a VPN, never access your bank account or vital records on an unsecured connection. Secured connections have a lock icon, usually located across from the name of the network.
Disable Wi-Fi, Bluetooth and Cellular Data when you're not using them. A hacker can't hack your phone if it's not connected to the internet. Follow the instructions in your user's manual or support section of the phone manufacturer's website. Turning on Airplane Mode is an easy way to turn off all communication on your phone with the push of a button.

Charge your phone on trusted USB ports. These include the ports on your computer and in your car (if applicable). Hackers can hack public USB charging ports, like the ones you may see in a coffee shop or airport, and steal personal information. For this reason, it's a good idea to bring your electrical outlet adapter in addition to your USB cable if you're traveling. Hackers can't hack your phone through your USB adapter.
Keep your operating system up to date. As soon as Apple or Android tells you an update is ready, download and install it. Many hackers take advantage of vulnerabilities in out-of-date operating systems. Updates patch these holes and make your phone more secure.
Password Sense
Choose a password that's hard to guess. Use complex combinations of letters, numbers, and symbols. The more complex you make the password, the more secure it is. Use uppercase letters in the middle of your password and throw in an obscure symbol to further complicate it. Avoid using obvious passwords like birthdays, anniversaries, or consecutive sequences like “1, 2, 3, 4, 5.” Don't use letters that spell out words such as your mom's maiden name or your pet's name. Password-protect your voicemail, Wi-Fi connection, and individual apps that you use for banking and email. When securing your voicemail, follow the instructions on your service provider's website. Consider using a Password manager. A password manager can generate and securely store passwords for all of your accounts. With a password manager, you'll only have to remember one very strong password.

Keep your passwords private. Use this as an unbreakable rule with everyone—best friends, partners, children, etc. When you're in public, glance around to make sure no one is looking over your shoulder. Finally, avoid entering a password near a closed-circuit television (CCTV) camera. You don't know who's watching on the other end.
Avoid auto-login. It might seem convenient for you, but it makes hacking as easy as opening your browser. Take the time to enter your usernames and passwords, especially on sites that you use for banking and other sensitive business. Type slowly to avoid getting locked out. If you're really pressed for time or just can't remember too many passwords, use a password manager. These programs store your passwords and fill them in when you access each site. You can lock the manager when you're not using it. Better yet: you'll only have to remember one password.
Use a variety of passwords. Having the same password for your email, bank account, and social media apps makes a hacker's job too easy. Take the time to think up creative mixtures of letters, numbers, and symbols for each account. Use a password generator backed up by a password manager to make this less of a burden on you. EXPERT TIP Brandon Phipps Brandon Phipps Technology Specialist Brandon Phipps is a Technology Specialist based in Bakersfield, CA. He is the owner of Second Star Technologies and specializes in Managed IT Services for small and mid-sized businesses in Bakersfield, CA. With over 23 years of experience, he offers expert cloud computing, cybersecurity, and network management solutions. Brandon is a committed community member and coach who leads and innovates in tech and sports coaching. His dedication to local businesses and communities is evident in his hands-on, tailored approach to IT solutions. Brandon Phipps Brandon Phipps Technology Specialist Avoid using the same password for multiple websites. If your login information on one website is compromised, hackers can potentially gain access to your accounts on other sites. Be sure to create unique passwords for each site to reduce your risk of being hacked, especially if a site seems like it has questionable security.
Change your passwords often. Create a password update schedule. Whether it’s weekly, monthly or quarterly, have a plan and stick to it. You could even enter a coded reminder in your calendar.
Protect Your Data
Don't share too much personal info on social media. It's okay to use your real name for networking but leave it at that. Never provide your address, phone number, mother's maiden name, etc. on your profile. Avoid even “safe” information like your favorite song or the book you're currently reading. Hackers can use any of this information to hack you and steal your identity.
Delete personal data from your phone. Photos can reveal a lot about you, allowing a potential hacker to steal your identity. Notes from your morning meeting can provide a wealth of info for industrial spies. Transfer your photos and any sensitive text-based files to your laptop or desktop computer. Reset your device when you want to recycle it (similar to reformatting a hard drive). First, perform encryption to scramble any data you might have missed. Then, follow the directions in your user's manual to reset your device.

Don't open suspicious emails. Merely clicking the link can give the sender a backdoor into your personal information. Delete the message immediately if you don't recognize the sender. If you do recognize them, hover over their name to make sure the email is legit. Webmail providers like Gmail will show you the sender's name and email address. EXPERT TIP Brandon Phipps Brandon Phipps Technology Specialist Brandon Phipps is a Technology Specialist based in Bakersfield, CA. He is the owner of Second Star Technologies and specializes in Managed IT Services for small and mid-sized businesses in Bakersfield, CA. With over 23 years of experience, he offers expert cloud computing, cybersecurity, and network management solutions. Brandon is a committed community member and coach who leads and innovates in tech and sports coaching. His dedication to local businesses and communities is evident in his hands-on, tailored approach to IT solutions. Brandon Phipps Brandon Phipps Technology Specialist Be careful when clicking on links or sharing your personal information online to avoid security breaches. Cybercriminals send emails with malicious links to deceive users. Verify the sender's identity and take precautions before clicking on any links or sharing personal information to prevent unauthorized account access.
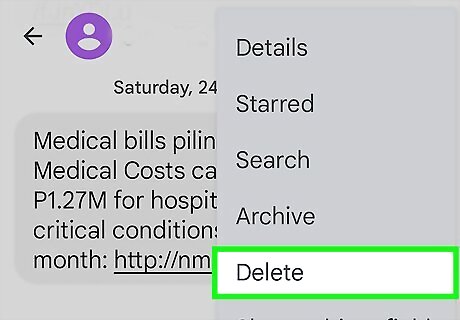
Avoid sending personal information from your phone. Consider the absolute worst-case scenario of your smartphone getting hacked, then work back from that. Stop using the phone for confidential information of any sort. If you receive confidential information, delete it immediately after reading it.

Backup your data. Save them to your desktop or laptop computer. After that, back up that data on an external hard drive or flash drive. If you've saved too much stuff on your phone, invest in an automated backup system that will save you the time of copying and emailing individual files.


















Comments
0 comment